The current implementation of airship-libvirt-gate is using sushy-emulator binary to emulate redfish. Sushy-emulator works only for http and also can’t authenticate users out-of-box if ran by itself. In order to check https and authentication the reverse-proxy was introduced. This approach had several drawbacks: 1) http still doesn’t check auth 2) to use apache for https only is too heavy solution for https This change converts reverse proxy to apache running sushy-emulator as wsgi backend, that gives an ability to check authentication for both http and https. We’re also getting rid of ad-hoc sushy-emulator service and using out-of-box apache service implementation. The code also introduces gathering of apache resulting configs and logs for quicker debug if needed. Right now authentication is disabled, since manifests are written in a way so they don’t use them. If it’s necessary to enable it, just set username here[1] PS There is ability to use apache for http-server [2], but it’s better to do as a separate PR [1] roles/airship-libvirt-gate/defaults/main.yaml [2] roles/http-fileserver Change-Id: I43b5bca41519c88b01535c156b2db0e9edaa81bb |
||
|---|---|---|
| .github | ||
| cmd | ||
| docs | ||
| manifests | ||
| pkg | ||
| playbooks | ||
| roles | ||
| testdata/k8s | ||
| tests/ansible | ||
| testutil | ||
| tools | ||
| zuul.d | ||
| .gitignore | ||
| .gitreview | ||
| .golangci.yaml | ||
| CONTRIBUTING.md | ||
| Dockerfile | ||
| go.mod | ||
| go.sum | ||
| LICENSE | ||
| main.go | ||
| Makefile | ||
| README.md | ||
| Vagrantfile | ||
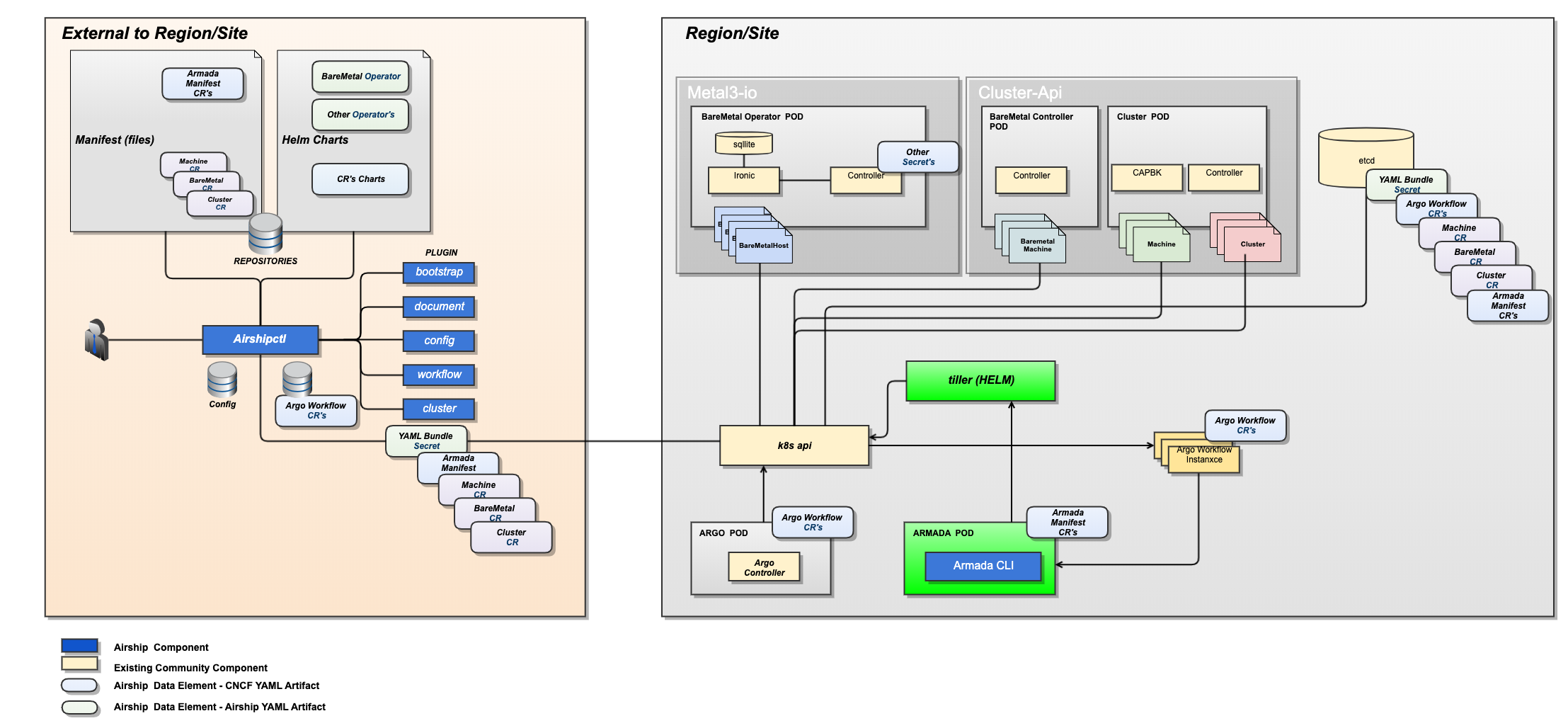
airshipctl
What is airshipctl
The airshipctl project is a CLI tool and Golang library for declarative
management of infrastructure and software.
The goal for the project is to provide a seamless experience to operators wishing to leverage the best of breed open source options such as the Cluster API, Metal3-io, Kustomize, Kubeadm, and Argo -- into a straight forward and easily approachable tool.
This project is the heart of the effort to produce Airship 2.0, which has three main evolutions from 1.0:
- Expand our use of entrenched upstream projects.
- Embrace Kubernetes Custom Resource Definitions (CRD) – Everything becomes an Object in Kubernetes.
- Make the Airship control plane ephemeral.
To learn more about the Airship 2.0 evolution, please check out the Airship Blog Series.
Contributing
This project is under heavy active development to reach an alpha state.
New developers should read the contributing guide as well as the developer guide in order to get started.
Architecture
The airshipctl tool is designed to work against declarative infrastructure
housed in source control and manage the lifecycle of a site.
Example Usage
In a nutshell, users of airshipctl should be able to do the following:
- Create an
airshipctlAirship Configuration for their site - sort of like a kubeconfig file. - Create a set of declarative documents representing the infrastructure (baremetal, cloud) and software.
- Run
airshipctl document pullto clone the document repositories in your Airship Configuration. - When deploying against baremetal infrastructure, run
airshipctl bootstrap isogento generate a self-contained ISO that can be used to boot the first host in the cluster into an ephemeral Kubernetes node. - When deploying against baremetal infrastructure, run
airshipctl bootstrap remotedirectto remotely provision the first machine in the cluster using the generated ISO, providing an ephemeral Kubernetes instance thatairshipctlcan communicate with for subsequent steps. This ephemeral host provides a foothold in the target environment so we can follow the standard cluster-api bootstrap flow. - Run
airshipctl cluster initinfra --clustertype=ephemeralto bootstrap the new ephemeral cluster with enough of the chosen cluster-api provider components to provision the target cluster. - Run
airshipctl clusterctlto use the ephemeral Kubernetes host to provision at least one node of the target cluster using the cluster-api bootstrap flow. - Run
airshipctl cluster initinfra --clustertype=targetto bootstrap the new target cluster with any remaining infrastructure necessary to begin running more complex workflows such as Argo. - Run
airshipctl workflow submit sitemanageto run the out of the box sitemanage workflow, which will leverage Argo to handle bootstrapping the remaining infrastructure as well as deploying and/or updating software.
As users evolve their sites declaration, whether adding additional
infrastructure, or software declarations, they can re-run airshipctl workflow submit sitemanage to introduce those changes to the site.
Project Resources
- Airship Website - airshipit.org
- Airship UI Project - opendev.org/airship/airshipui
- airshipctl Issue Tracker - https://github.com/airshipit/airshipctl/issues